Now LIVE! Check out the NEW Zoom Feature Request space to browse, vote, or create an idea to enhance your Zoom experience.
Explore Now-
Products
Empowering you to increase productivity, improve team effectiveness, and enhance skills.
Learn moreCommunication
Productivity
Apps & Integration
Employee Engagement
Customer Care
Sales
Developer Tools
- Solutions
By audience- Resources
Connect & learnHardware & servicesDownload the Zoom app
Keep your Zoom app up to date to access the latest features.
Download Center Download the Zoom appZoom Virtual Backgrounds
Download hi-res images and animations to elevate your next Zoom meeting.
Browse Backgrounds Zoom Virtual Backgrounds- Plans & Pricing
- Solutions
- Product Forums
AI Companion
Empowering you to increase productivity, improve team effectiveness, and enhance skills.
Zoom AI CompanionBusiness Services
- Event Forums
- Customer Success Forum
- Quick Links
- Zoom
- Customer Success
- Customer Success Forum
- Re: Year in review: What our 2023 Bug Bounty progr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Year in review: What our 2023 Bug Bounty program means for Zoom security in Customer Success Forum
- Zoom achieves new global security standards for core products with ISMAP registration in Customer Success Forum
- Revolutionizing Communication with Zoom Phone: Green Bay Area Public School District in Customer Success Forum
Year in review: What our 2023 Bug Bounty program means for Zoom security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-08 06:05 PM
Zoom’s Bug Bounty Program incentivizes the discovery and responsible disclosure of security vulnerabilities. Here's a look at the past year's highlights.
Security is a constant focus at Zoom and an ongoing investment we remain committed to through a variety of programs and initiatives. The Zoom Bug Bounty Program is one such initiative aimed at enhancing online security and a shining example of the collaboration, innovation, and continuous improvement that encompasses the entire Zoom community. Since 2019, we’ve been actively working with the researcher community, and now, we are thrilled to announce we have awarded more than $10 million in bug bounty payments to help fortify Zoom's defenses and protect the privacy and security of our users.
Zoom’s Bug Bounty Program is designed to incentivize the discovery and responsible disclosure of security vulnerabilities. In the past two years, we have implemented a streamlined process to ensure prompt reactions and responses to all security reports. Once a bug has been detected and submitted by one of our 800+ researchers, our security team will have the report analyzed, reproduced, and submitted to the correct internal development team for remediation, on average, within just a few hours.
Over the past 3+ years, Zoom has been driving down the cost per report of program operation, while at the same time increasing the identification of vulnerabilities, which have a tangible impact on our platform. In just three years, we’ve decreased the cost per a valid report by 40% and observed more than double the reported submissions.
Looking back at our 2023 accomplishments
VISS
In January 2023, the Bug Bounty team committed to building, refining, and releasing an innovative new mechanism to measure the real-world impact the exploitation of a vulnerability has on a system. The March implementation of the Vulnerability Impact Scoring System, or VISS, was the result of this collaborative effort that we op...on Github.
Zoom has been utilizing VISS for more than a year and has seen growing interest from other bug bounty teams looking for a more objective measure of vulnerability impact. To date, the collaboration and feedback about VISS has been positive. Security researchers are contributing feedback as well, which increases the colla...
“VISS allows us to tailor the security researchers’ work so that we’re focused on the things that are most important, that have the highest level of impact, and then our payouts are oriented accordingly,” explains Michael Adams, Zoom CISO. “Not only do I want to pay accordingly, but I want to incentivize accordingly, and if I can’t provide clarity within my scoring system, it’s hard for them to understand. We’re now able to provide a certain degree of clarity,” says Adams.
To delve into the specifics – and to try out Zoom’s implementation of the VISS calculator – check out the complete VISS specification.
HackerOne
We were also thrilled to be a sponsor of this year’s HackerOne H1-4420 event, which took place on June 22, 2023, at CodeNode in London. This event provided us with an invaluable opportunity to collaborate with over 90 of the most talented ethical hackers from 41 countries, all working together to help enhance the security of the Zoom platform. By actively engaging with this community, we can not only mitigate risks but also foster innovation and continuously improve our services. Here’s a recap of the event.
Bug bounty awards
2023 was a big year for us as we made bug bounty award payments of more than $2.4 million for 1,000+ separate valid reports submitted by more than 200 different security researchers. This brought the cumulative total bug bounty awards to more than $10 million.
Security remains a top focus for the road ahead
As artificial intelligence and machine learning are more tightly integrated into Zoom products, the Zoom Bug Bounty team has been busy working with many of o...
In addition to our focus on AI, we have a robust set of features slated for release this year as part of our 2024 roadmap. With this in mind, we look forward to a wave of new report submissions from our “Spring BREAKAGE” promotion, which began April 1, 2024, and runs throughout April. Several new features have been added to the testing scope, and bounties have been increased for this promotion.
If you’re interested in helping to make Zoom more secure, email your HackerOne profile name to *********** or visit the Zoom careers page to review the open positions within the Trust and Security teams. Happy hacking!
To learn more about Zoom privacy and security, visit our Trust Center. Found a bug? Submit a vulnerability issue here.
- Topics:
-
Adoption & Onboarding
-
Best Practices
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-12 11:42 PM
How about the security bug of this flippin read.ai, that shows up when no one has signed up for it and can't be gotten rid of. There are a lot of people asking in the community forum and no one from Zoom answering.
Where did read come from? Get rid of it!!! It is ridiculous that the only rix offered is to log in to an app I never signed up for to delete it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-18 09:53 AM
Hi @aluna
I understand the frustration you're experiencing. It's possible that someone else invited to your call has also enabled Read. They don't necessarily need to attend the meeting; just being invited is enough. Read can only join if a Read user invited to the meeting adds it.
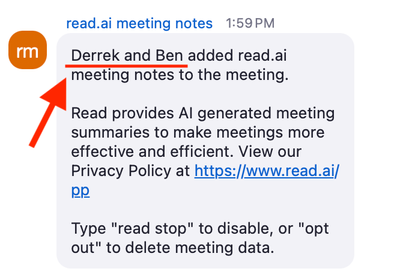
Each meeting platform supported by Read has a built-in chat function. When Read joins a meeting, it sends a message to the chat that looks something like this:
If you see your own name listed, it means you have a Read account. In this case, you should:
1. Search your emails for messages from support@e.read.ai, such as the "Welcome to Read!" email sent to new users.
2. Check the primary email address of your Read account in the "to:" line.
3. If you have multiple email addresses, check all your inboxes.
4. If you used single sign-on (SSO) like Microsoft or Google to create your account, try logging in using those options if you're unable to with your email and password.
Additionally, you can remove an automated meeting tool from a meeting if you don't want it to record the content. Click the Security icon in the Zoom Meeting window and then click Remove Participant.
Another method to prevent automated tools from joining is to enable a waiting room for your entire account or a specific user within your account. This way, you only admit participants, not automated tools.
For more information on preventing Read.ai from joining meetings, check out: How do I remove or stop Read from joining meetings?
Let me know if this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-18 11:19 PM
Carla, I responded in the main thread since this is just a copy and pasted reply that you sent.
Please view the response. None of this is a fix.
Is Zoom going to do something about this app that seems to have taken on a life of its own?